SSH: Difference between revisions
(Created page with "=Summary= SSH (Secure Shell) is a cryptographic network protocol used to securely access and manage devices over an unsecured network. It is commonly used to log into remote servers, execute commands, and transfer files securely. SSH encrypts the communication between the client and server, ensuring that sensitive data (like passwords) is protected from eavesdropping and tampering. The current gold standard is ed25519, so you'll want to primarily use a ed25519 keypair....") |
|||
| (One intermediate revision by the same user not shown) | |||
| Line 11: | Line 11: | ||
* Sharing your '''Public''' Key is fine and does not compromise any security. | * Sharing your '''Public''' Key is fine and does not compromise any security. | ||
=SSH Process= | |||
[[File:Ssh connection.png|500px]] | [[File:Ssh connection.png|500px]] | ||
=Common Tasks= | |||
==Creating a Keypair== | ==Creating a Keypair== | ||
| Line 60: | Line 62: | ||
To use your keys to log into a typical Linux '''server''', you'll need to copy your '''Public Key''' into your <code>~/.ssh/authorized_keys</code> file on the '''server'''. This file should already exist, but if you have to create it, be sure to give it 0600 file permissions. The <code>~/.ssh/</code> directory itself should have 0700 permissions. Then you'll need your '''Private Key''' copied to your '''client''' box and referenced appropriately in your SSH software (e.g., SecureCRT, PuTTY, etc.). | To use your keys to log into a typical Linux '''server''', you'll need to copy your '''Public Key''' into your <code>~/.ssh/authorized_keys</code> file on the '''server'''. This file should already exist, but if you have to create it, be sure to give it 0600 file permissions. The <code>~/.ssh/</code> directory itself should have 0700 permissions. Then you'll need your '''Private Key''' copied to your '''client''' box and referenced appropriately in your SSH software (e.g., SecureCRT, PuTTY, etc.). | ||
== | ==Manipulating Keys== | ||
===Generate Public Key from Existing Private Key=== | |||
ssh-keygen -y -f id_ed25519 > id_ed25519.pub | |||
or | |||
ssh-keygen -y -f id_rsa > id_rsa.pub | |||
=SecureCRT= | |||
{{ToDo| | {{ToDo|This section.}} | ||
Revision as of 16:25, 21 January 2025
Summary
SSH (Secure Shell) is a cryptographic network protocol used to securely access and manage devices over an unsecured network. It is commonly used to log into remote servers, execute commands, and transfer files securely. SSH encrypts the communication between the client and server, ensuring that sensitive data (like passwords) is protected from eavesdropping and tampering.
The current gold standard is ed25519, so you'll want to primarily use a ed25519 keypair. Unfortunately, not all vendors have updated their ways to play nicely with ed25519, forcing us to sometimes use legacy RSA keypairs.
- Everyone should have a SSH keypair.
- For legacy compatibility, it's a good idea to have both an ed25519 keypair and an RSA keypair (but prefer ed25519).
- For simplicity and convenience, use the same keypair on all NCT systems.
- Guard your Private Key like your cell phone or car keys - never give it to anyone.
- Sharing your Public Key is fine and does not compromise any security.
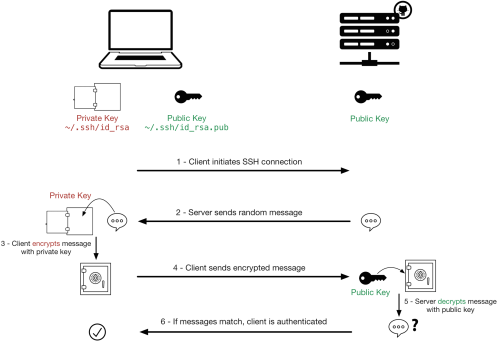
SSH Process
Common Tasks
Creating a Keypair
![]() Warning: NEVER give your Private Keys to ANYONE. On the other hand, your Public Key can be handed out freely.
Warning: NEVER give your Private Keys to ANYONE. On the other hand, your Public Key can be handed out freely.
![]() Info: Your Public Key is the one that gets transferred to the Server you're connecting to. Your Private Key always stays at home, with you (the client).
Info: Your Public Key is the one that gets transferred to the Server you're connecting to. Your Private Key always stays at home, with you (the client).
ed25519
Creating
- SSH into a Linux box. Corelogs would be perfect for this.
- In your home directory, run
ssh-keygen -t ed25519.- Follow the prompts. If you enter a passphrase, you'll need to enter it EVERY time you log in using your SSH keypair.
- Note where your keys get stored by default:
- Private Key:
$HOME/.ssh/id_ed25519 - Public Key:
$HOME/.ssh/id_ed25519.pub - The above are standard naming conventions, and should be followed for best compatibility with all the things.
- Private Key:
Using
To use the keypair to log in to something, you'll need to save the Private Key to whatever client you plan to connect from (e.g., your VDI), and upload the Public Key to whatever you plan to connect to (e.g., a Server).
![]() Warning: Take care where you copy your Private Key to - if anyone else gets access to it, they can impersonate you.
Warning: Take care where you copy your Private Key to - if anyone else gets access to it, they can impersonate you.
To use your keys to log into a typical Linux server, you'll need to copy your Public Key into your ~/.ssh/authorized_keys file on the server. This file should already exist, but if you have to create it, be sure to give it 0600 file permissions. The ~/.ssh/ directory itself should have 0700 permissions. Then you'll need your Private Key copied to your client box and referenced appropriately in your SSH software (e.g., SecureCRT, PuTTY, etc.).
RSA
Creating
- SSH into a Linux box. Corelogs would be perfect for this.
- In your home directory, run
ssh-keygen -t rsa.- Follow the prompts. If you enter a passphrase, you'll need to enter it EVERY time you log in using your SSH keypair.
- Note where your keys get stored by default:
- Private Key:
$HOME/.ssh/id_rsa - Public Key:
$HOME/.ssh/id_rsa.pub - The above are standard naming conventions, and should be followed for best compatibility with all the things.
- Private Key:
Using
To use the keypair to log in to something, you'll need to save the Private Key to whatever client you plan to connect from (e.g., your VDI), and upload the Public Key to whatever you plan to connect to (e.g., a Server).
![]() Warning: Take care where you copy your Private Key to - if anyone else gets access to it, they can impersonate you.
Warning: Take care where you copy your Private Key to - if anyone else gets access to it, they can impersonate you.
To use your keys to log into a typical Linux server, you'll need to copy your Public Key into your ~/.ssh/authorized_keys file on the server. This file should already exist, but if you have to create it, be sure to give it 0600 file permissions. The ~/.ssh/ directory itself should have 0700 permissions. Then you'll need your Private Key copied to your client box and referenced appropriately in your SSH software (e.g., SecureCRT, PuTTY, etc.).
Manipulating Keys
Generate Public Key from Existing Private Key
ssh-keygen -y -f id_ed25519 > id_ed25519.pub
or
ssh-keygen -y -f id_rsa > id_rsa.pub
SecureCRT
![]() To Do: This section.
To Do: This section.